We met Google’s Security Princess. Here’s what she had to say.
When a vision becomes a reality
During my freshman year of high school, my computer science teacher showed our class a Code.org video on computer security that featured a very special woman who would soon become my security role-model: Parisa Tabriz.

ICYDK (In Case You Didn’t Know), Parisa is a Director of Engineering at Google. She is also the current Director of Google Chrome Security (“Browser Boss”), as well as the leader of Project Zero, Google’s elite security research unit, tasked on finding the latest zero-day vulnerabilities in Google products. I know, she’s PRETTY COOL.
I still remember my teacher, who had known about the work I had been doing in security, turning to me during the video played in class, saying, “Have you met her yet, Kyla?” I chuckled a little to myself, thinking about the absurdity of the thought of someone like me entering the vision of someone of Parisa’s caliber and respected position. However, after that one moment, it became a goal of mine to work so hard in security that one day, it would feel right to meet Parisa. Never did I imagine that after my sophomore year of high school, sitting before me at a worn table at a quiet corner coffee shop, would be the adventure-chasing, Black-Hat-keynoting, future-driven, Gelato-University-alumna and security-extraordinaire: the one-and-only, Parisa Tabriz.
The video that started the quest to Parisa:
One week after our nonchalant two-hour meeting, I was still feeling the reverberations of passion, energy, and drive from our conversation. The meeting had made Parisa even more of a guiding figure and role model for me as a student and a security-supergirl, and you’ll quickly learn why as you read our conversation. Check out this special feature, as we dive headfirst into the future of global cybersecurity, Google’s current/future initiatives, and Parisa’s origin story here:

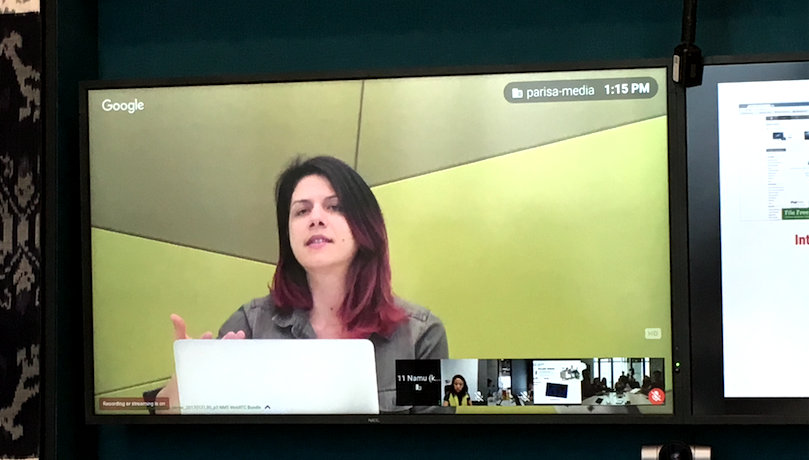
Parisa and I met during my time in the Bay Area over this past summer. *internally fangirls*
Coffee-side Chat: Parisa Tabriz
Kyla Guru: So first off, I wanted to take you back to the time when you decided to turn your attention towards security. What inspired you to look towards cybersecurity as a career option?
Parisa Tabriz: I actually wasn’t exposed to computers or coding until college; I actually got my first computer as a freshman in college. I ended up choosing engineering as a major at the University of Illinois because I had to choose something. I liked math, I liked science, and I also knew I didn’t want to do medicine. I also really liked art. Separate to courses, I set off to make a personal webpage, which prompted me to learn HTML, Javascript, and CSS through free online tutorials.
One day, one of the websites I had made got hacked–I noticed some Viagra ads being served from my website, and immediately knew something was wrong. A hacker had exploited a PHP vulnerability in code I had written, and that got me interested in learning how that happened and how one could prevent that from happening.

Source: CNEWSquare
Shortly afterwards, I joined a security club at U of I, where I learned from other members and taught them about web security. At the time, web security was considered pretty lame, but the club exposed me to a lot of other aspects of industry and I could teach others about what I had learned that way too. Then, one summer, I took on an internship at Sandia National Labs in California, which exposed me to people working full-time in security and various research topics. This was the first time that I realized I could do security as a long-term career. My first plan was to go to grad school, but I then took on an internship at Google, joining their security team. It was rewarding to work on a real product that I was using and my friends and family were using too.
Diversity in security is lacking, and that will impact our effectiveness in solving problems for the world. We do need more designers, lawyers, policymakers.
KG: That’s awesome. I’m curious: did you have any role models in security that you looked up to when you were entering the field?
PT: I actually followed a blog in college by Michał Zalewski, who went by the name lcamtuf, the name of a video game cheat code. I implemented one of the pieces of research he had done for a computer science project. Then, we worked together for over 10 years at Google! He’s incredibly smart, modest, creative, and mostly self-taught; he taught himself English by reading Intel manuals!
KG: Wow. It’s interesting you bring up creativity as a key characteristic of a security expert. What role do you think having an abstract design mindset has on security?
PT: Well, there’s no handbook for security. A lot of the time, you have to think like someone who’s trying to break the system moreso than build it. I often give a “how would you break into the vending machine?” thought exercise when I talk about hacking and security because it’s something very approachable to people. The answers can really vary. There’s some typical ones like the “dollar-on-the-string hack,” but there’s also some really creative answers. One time, someone said they would fill the machine up with water so that the snacks would rise to the top. Security is thinking about how you mitigate potential weak points in an efficient, practical way since defenders don’t have unlimited time and resources.

Source: Fossbytes
KG: That makes sense! Also, in an article for Medium, you mentioned that a job in security is actually “not as fast-paced” as it looks in the movies. What does a typical day look like for you at the moment?
PT: My job is actually very different now than it was when I began at Google. Now, I am the manager of about 200 people, which is very different than how I started as a software engineer. I used to have 1-3 meetings a week. Now, I have probably 8-15 meetings a day!
When I started, I worked as what they call an “individual contributor,” writing code and reading code. Now, as a manger, I’m like an interrupt handler. I handle things that slip through or get stuck in the cracks or my team. For example, sometimes I’ll need to make a decision because it’s really not obvious which way to go. On Chrome, we want the browser to be secure, but also fast, stable, and really easy to use. This often introduces tricky tradeoffs, especially when you have specific teams going about it at a specific angle. Sometimes, there’s one thing we should do with security, but it will have an impact on performance. That’s also a big challenge about security in the real-world. The most secure computer is one that’s not connected to the Internet; that’s also not a very useful computer. Building useful technology that’s also fast, secure, and privacy preserving sounds nice, but is really tricky to do in practice.
What I worry about more than attacks about controlling machines is attacks about influencing public opinion.
So my typical day: I wake up pretty early. I have the same breakfast with coffee. I go to my email inbox and calendar, which dictates what my day is, whether that be updates on projects or handling an incident. At the end of the day, I exercise, maybe read a book or go for a walk with my husband, and then do another big sweep of my inbox: I have a team in Germany and sometimes work with teams in Asia, so I’m working with people in lots of different time zones.
Whatever I’m doing with the teams, I always make sure to have frequent meetings to make sure that Chrome is going in the right direction and we are all on the same page.
Source: Rapler
KG: Were you working on the new HTTPS initiative that Google recently put into place? (Check out the new Google Chrome feature that came out on July 24th!)
PT: Yes! I started that effort in maybe 2014, about 4 years ago. I’m very proud of it because it’s been quite a journey. It’s not done yet, because at some point, we want to remove any kind of green lock icon on safe sites so that you only see a negative warning. We want to focus on the content and not the outside of Chrome because users want content. The more simple we can make the “Chrome” part of the browser, the better.
We can’t just react anymore. We have to proactively set aside some amount of resources based on what we know today.
KG: So neat. I was actually talking to my dad this morning about getting an SSL certificate for my website, because we don’t have one yet (Update: Check out the little green lock, guys! We got. it. done. Go BNBCE!).
So, a little birdie told us that you will be delivering the keynote at Blackhat in Las Vegas this year! Major congratulations are in order. Could you share a little about what you will be speaking about?
Watch the recording of Parisa’s keynote here!
PT: Thank you! As of right now, I’ll be talking about how we need to work together on defense to improve security going forward and how we aren’t doing nearly enough right now. Despite security improving in a lot of ways over the last 10 years, the complexity of the landscape is also growing. I’ll be sharing three pieces of advice on how we need to work together to find solutions.
- The first is that we need to shift the focus to tackle the root problem, more than the symptoms. In the medical world, they say “treat the illness, not the symptom” a lot, and it’s the same here. Instead of playing whack-a-mole with bugs, think about the weakness of architecture and systems and even processes and people.
- The second is setting milestones to work toward and celebrating when you hit those milestones. HTTPS is an example of this I’ll talk about. Change takes a long time, especially projects with a large impact. Persevering means working as if it’s a marathon, rather than a race.
- The third is how we need to invest in protecting against future attacks, today. We can’t just react anymore. We have to proactively set aside some amount of resources based on what we know today.

Source: The Telegraph
KG: I’m so excited to watch the live stream! And yes, I hear what you are saying. I think security needs to start on the hardware side, from the time of design. Software cannot always solve all our problems!
PT: Totally and Google is actually talking to Intel right now, thinking about how to mitigate Speculative Execution attacks. For them, what’s tricky is that it takes many, many years to develop a new chip.

Source: Adam Shostack
I’ve learned that some of the people I looked up to most were the most humble and modest people.
KG: Definitely. I would say BNBCE works a lot with the user population. So how do you think users can be more prepared for attacks of tomorrow?
PT: I think one of the biggest concerns for the future is account hijacking, which often stems from users using the same password in multiple places. I recommend people use two-factor authentication when it’s available and figure out a way to manage strong, unique passwords. Taking on the task of memorizing all of them leads to repetition of passwords. I save passwords in Chrome, which can also generate a random strong password for you. Also, you could look into password managers.
Another thing is simply thinking about the software you are using and what the security reputation is of that software. And, of, course, being a little paranoid helps.
Also, installing updates is important! However, malware authors try and disguise malware as updates. So one thing I’m proud of with Chrome is that it automatically updates, taking the decision off of the user. You have to make it so that users don’t have to think about choosing whether to install an update or not. The more complicated or cumbersome it is, the less likely people will do it.

Source: She Secures
For instance, with the WPA2 Krack, setting up a wireless router and resetting it has to be easy, or else not all citizens can take precaution.
The most secure computer is one that’s not connected to the Internet; that’s also not a very useful computer.
KG: Nice. Google employees use security keys, right? Is that only for employees?
PT: Yes, security keys are used internally. In many ways, the physical USB key is more secure than 2-factor authentication, since a 2nd factor can be phished too. You can also buy them from Yubiko for families or friends too! You could also loose this, but practically, the threat of a burglar is very different than that of an online hacker. Not the most practical threat for most people.

Google promotes using Yubikey physical USB keys as a form of two-factor authentication for all of it’s employees. Source: Android Authority
KG: How do you see attacks changing in the coming years on both the corporate side and on critical public infrastructure?
PT: What I worry about more than attacks about controlling machines is attacks about influencing public opinion. I worry about abuse a lot. I think we will see how social networks can be used for good in getting messages out, but also in ways we are not totally ready to manage.
I think we need it (hope). There’s a lot of problems in the world so we really have to have it.
KG: Yes, with that, another rising concern is with cyber-warfare. It’s crazy to think that the our country could be a victim. What do you think Google’s role is in combating these issues, and how do you think we should respond?
PT: The delineation between the private sector and national security is not practical or possible. So much of the nation and world’s communication happens on private services and Google definitely does have a role in national security. At the same time, Google is an international company, which brings about both collaboration and tension between individual country’s’ national security. Also, when national security wants information on citizens, Google has to protect their customers. Figuring out the balance depends on the situation and there’s very few people who are well-versed in both. A lot of technologists don’t know about policy and a lot of policymakers don’t understand how technology works: communication between the two is integral.

Source: Little Web Giants
KG: How would you say young people interested should practice and fine tune their cybersecurity skills for the future?
PT: Get involved with different hacker playgrounds, since reading is not the same as doing in cybersecurity. There’s a ton of intentional apps with holes in them, so find the holes and try to fix them. Learn about reverse engineering, try different CTF’s. Also, try getting some small job experiences first, like helping local government set up a new web server or going through OWASP’s training guide.
(Check out the detailed article Parisa wrote on this topic here: https://medium.freecodecamp.org/so-you-want-to-work-in-security-bc6c10157d23)
KG: Alright: do you have any cybersecurity reads/movie recommendations?
PT: Most of the Hollywood movies with cyber don’t air on the side of reality, which, quite honestly, I don’t mind, since it’s a bit of an escape from reality. A lot of security is reading documentation or log files, which isn’t exactly movie material. Some of my favorite TV shows are Mr. Robot and Halt and Catch Fire. Movies would be Hackers, Sneakers, and War Games.
In terms of good reads, I would recommend Tangled Web by Michał Zalewski. I also follow a bunch of blogs. (*squeals internally, hoping for Parisa to now follow our blog*)
Change takes a long time, especially projects with a large impact. Persevering means working as if it’s a marathon, rather than a race.
KG: Awesome. Now, going back to the person you are in the industry: What does it feel like being so young in the cybersecurity industry? How about being a women in the cybersecurity industry?
PT: I feel much more comfortable now, having been working in security for over a decade, in the fact that I don’t know everything. I also now understanding that that’s how everyone is like as well. There’s a tendency for people in the industry to have an aura of eliteness, but now, I’ve learned that some of the people I looked up to most were the most humble and modest people. I also now believe that having a breadth of interests and caring about users and some of the non-technical aspects of security (e.g. business) is a good thing. I used to feel that it came at the cost of going deep on one specific topic, but there’s benefits to breadth.
So much of the nation and world’s communication happens on private services and Google definitely does have a role in national security.
As a women, I had two brothers, and I played a lot of sports growing up. I was already exposed to male-dominated environments, so I honestly wasn’t aware of the challenges that being a female in STEM brought until I became a manager of a team of all men at Google. Hearing other people’s toxic experiences has made me realize that there are still many problems. Diversity in security is lacking, and that will impact our effectiveness in solving problems for the world. We do need more designers, lawyers, policymakers. I feel really lucky to be where I am today.

The Google “hired hackers” team. Source: Nature Blogs
KG: For me, I could feel this change happening when running GirlCon and I still remember feeling so energized and hopeful. In fact, a large part of that energy was from meeting women like yourself who simultaneously live everyday with focused purpose and elegance. During my research, this was underlined even more as someone said about you, “few make the Forbes 30 under 30 list on a Friday, head out for a weekend climb in the icy mountains of the Sierra Nevada, hop over to Singapore on Tuesday to orchestrate a hacker competition, and still show up in the office back on Thursday morning with home-baked cookies and a smile, ready to go out and fix the internet. That’s Parisa for you.” (Maarten Van Horenbeeck, Proudly found from LinkedIn stalk). How do you balance your stressful, high-impact work life with your adventurous side?
PT: Climbing and going outdoors is an important part to me not going crazy. This could be anything for someone else! People who really enjoy making music, pottery, baking, or crafts. For a software programmer or computer engineer, you don’t get to touch many things you make. Since I always like to have my hands in a lot of different things, baking and crafts are a fun way to balance my love for technology. Also, being busy is very important: otherwise I would just sleep! I always stay curious and love to learn.

Source: Little Web Giants
KG: I love it. Okay, now it’s time for rapid fire. What’s you social media of choice?
PT: Twitter for articles and news, Facebook for friends and family connections, Instagram for photo sharing.
KG: What would you make if you could make one tech device for any purpose?
PT: An attractive identity provider token management that is on you. Whether it’s a necklace or a ring, something where you would be able to walk up to any digital surface, use it as “you,” and leave no traces left behind when you’re done. I like the idea of carrying your personal digital state around with you in a convenient, attractive, and ubiquitous way.
Security is thinking about how you mitigate potential weak points in an efficient, practical way since defenders don’t have unlimited time and resources.
KG: Favorite Animal?
PT: A cat. I have two of them. They’re more interesting that plants and fish, but not as much work as a dog.
KG: Constant source of motivation?
PT: Impact on the world. I like working on Chrome at Google because a lot of people use it: having a positive impact on the world is important to me.

Source: Racked SF
KG: If you could make a signature fragrance, what would it be?
PT: Ah, good question. *a sip of coffee and some ponders later* I drink a lot of coffee and eat a lot of peanut butter. Not sure how great they would be together, but I would at least like to explore that!
KG: Favorite word?
PT: Hope. I think we need it. There’s a lot of problems in the world so we really have to have hope.
KG: Yes! And Gen-Z has to be the generation that delivers that hope.
PT: Yes!
This interview has been edited for length and clarity.
Key Takeaways
 Talking to Parisa shared the perspective of a leader working on the forefront of the incredibly growing and expanding industry of cybersecurity: of someone who fights the bad actors on a daily basis for the purpose of the greater good. While I learned a lot more about Google’s security initiatives, I also learned about Google’s role in cyber-problems impacting our world, and Parisa’s perspective on the global privacy and security matters that impact our lives. I even got to hear what Parisa believes we can do, as citizens of this world, to protect ourselves and strengthen the global network. It was exciting, energizing, and humbling to take in her perspective, and relate to her on so many levels as a women in tech, an advocate for user-end security, and a believer in using security as a means to inspire hope for our future.
Talking to Parisa shared the perspective of a leader working on the forefront of the incredibly growing and expanding industry of cybersecurity: of someone who fights the bad actors on a daily basis for the purpose of the greater good. While I learned a lot more about Google’s security initiatives, I also learned about Google’s role in cyber-problems impacting our world, and Parisa’s perspective on the global privacy and security matters that impact our lives. I even got to hear what Parisa believes we can do, as citizens of this world, to protect ourselves and strengthen the global network. It was exciting, energizing, and humbling to take in her perspective, and relate to her on so many levels as a women in tech, an advocate for user-end security, and a believer in using security as a means to inspire hope for our future.
Not only did speaking with Parisa expand my perspective and knowledge on the topic of security, I also got to connect with Parisa about increasing the engagement of young people in the field and uniting a community around security: a topic I hold close to heart. To say the very least, I am constantly and daily fueled by Parisa’s technical expertise and passion for high-impact work and cannot wait to see how we collaborate further in the future. Parisa and I both share an urge to impact the world, a belief in proactive precaution rather than reactive action, and a stead hope that solutions are on the way.
Thank you deeply, Parisa, for taking the time to sharing your brilliance and vision with us and the world. Thank you for the work you lead everyday to let us have information at our fingertips. Thank you for being a powerhouse role model.
Not all heroes wear capes, some wear white hats.
Stay safe and happy surfing!
Sincerely,
Detective Safety


